
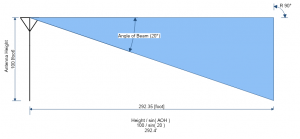
A lot of people don’t realize that high gain antennas achieve their gain by narrowing the vertical beam of the antenna. For instance the Laird FG8246 antenna is listed as having 6 dBi gain at the horizon, but it drops to no gain at +/- 20o angle off of horizontal (AOH) and drops even more beyond that angle.
So, what does that mean in real life? Well, let’s imagine that you have that antenna mounted on a 100′ tower. The 20o beam will touch the ground roughly 300′ from the base of the tower. The formula to calculate the horizontal distance from the base to the intersection is:
Height * sin( 90 ) / sin( AOH )
In the diagram above, the area below the blue triangle will be limited in connectivity. If there are radios in that area, they may be “overlooked” by a high gain antenna, especially if the antenna is mounted on a high tower on the top of a mountain. You can use the formula above to calculate the distance from the tower the antenna should be most effective.
HALF POWER BEAM WIDTH (HPBW)
This is a specification you may see on some antennas. It is the angle where the antenna is at 1/2 of it’s maximum gain. So for instance, a 8.15 dBi antenna should have a HPBW of 19.5o (or 9.75o AOH). Basically, a 2.15 dBi antenna has a HPBW of 78o and for every 3 dBi of gain, the HPBW is cut in half.
| Maximum Gain | HPBW | AOH | 100′ Tower | 500′ Tower |
| 2.15 | 78o | 39o | 159′ | 795′ |
| 5.15 | 39o | 19.5o | 300′ | 1500′ |
| 8.15 | 19.5o | 9.75o | 590′ | 2950′ |
| 11.15 | 9.75o | 4.9o | 1,170′ | 5850′ |
Where more is less….
Ok, now let’s look at a situation where having a higher gain antenna could SERISOUSLY hurt your coverage. Imagine a 100 story building in the middle of NYC. On top of that building they have a 11.15 dBi gain antenna on a 20′ mast. Assuming an average of 14′ per floor * 100 floors + 20′ = a ‘tower’ height of 1420′. Plugging that into the calculation, the HPBW would touch ground over 3 miles away from the building.



